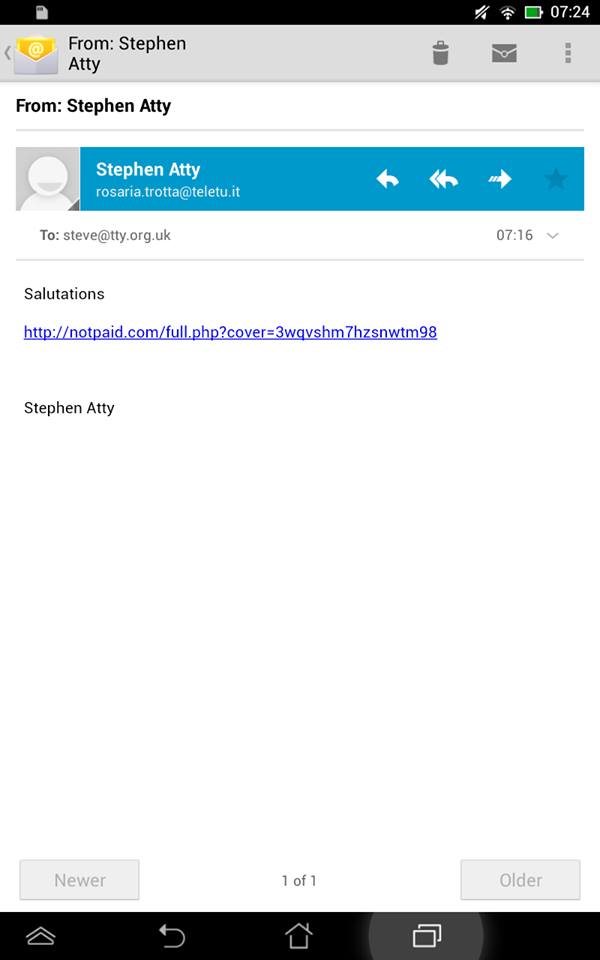
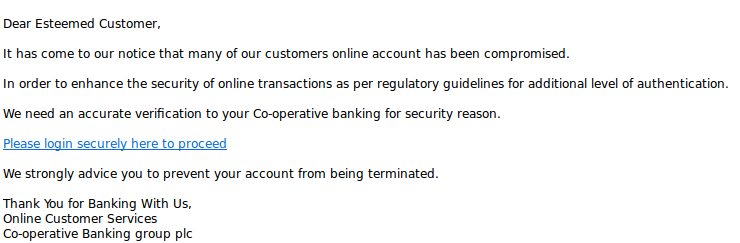
2014-10-23 04:39:51,514 fail2ban.actions: WARNING [apache-wplogin] Ban 198.23.155.76
2014-10-23 11:02:05,033 fail2ban.actions: WARNING [postfix] Ban 111.249.35.151
2014-10-23 12:44:57,061 fail2ban.actions: WARNING [sasl] Ban 63.152.242.19
2014-10-23 12:47:16,215 fail2ban.actions: WARNING [postfix] Ban 49.230.184.69
2014-10-23 12:49:02,731 fail2ban.actions: WARNING [postfix] Ban 185.7.100.97
2014-10-23 12:49:41,087 fail2ban.actions: WARNING [postfix] Ban 103.229.84.194
2014-10-23 12:51:27,010 fail2ban.actions: WARNING [postfix] Ban 59.94.15.250
2014-10-23 12:51:51,892 fail2ban.actions: WARNING [postfix] Ban 94.20.224.54
2014-10-23 12:52:20,205 fail2ban.actions: WARNING [postfix] Ban 190.178.92.83
2014-10-23 12:52:38,306 fail2ban.actions: WARNING [postfix] Ban 69.198.18.202
2014-10-23 12:52:50,037 fail2ban.actions: WARNING [postfix] Ban 118.102.169.44
2014-10-23 12:53:31,943 fail2ban.actions: WARNING [postfix] Ban 79.97.188.35
2014-10-23 12:54:24,326 fail2ban.actions: WARNING [postfix] Ban 5.42.193.34
2014-10-23 12:54:24,600 fail2ban.actions: WARNING [postfix] Ban 117.204.153.6
2014-10-23 12:54:52,445 fail2ban.actions: WARNING [postfix] Ban 122.171.119.247
2014-10-23 12:57:45,569 fail2ban.actions: WARNING [postfix] Ban 117.204.143.124
2014-10-23 12:57:58,709 fail2ban.actions: WARNING [postfix] Ban 154.70.236.29
2014-10-23 13:03:41,906 fail2ban.actions: WARNING [postfix] Ban 139.216.57.220
2014-10-23 13:04:55,166 fail2ban.actions: WARNING [postfix] Ban 116.33.2.37
2014-10-23 13:06:18,096 fail2ban.actions: WARNING [postfix] Ban 123.176.22.30
2014-10-23 13:08:37,083 fail2ban.actions: WARNING [postfix] Ban 77.234.44.138
2014-10-23 13:11:02,561 fail2ban.actions: WARNING [postfix] Ban 105.186.68.107
2014-10-23 13:12:33,356 fail2ban.actions: WARNING [postfix] Ban 74.112.58.73
2014-10-23 13:13:51,867 fail2ban.actions: WARNING [postfix] Ban 179.8.149.180
2014-10-23 13:14:14,576 fail2ban.actions: WARNING [postfix] Ban 197.253.66.208
2014-10-23 13:14:32,456 fail2ban.actions: WARNING [postfix] Ban 82.199.201.242
2014-10-23 13:15:55,821 fail2ban.actions: WARNING [postfix] Ban 67.231.35.166
2014-10-23 13:16:44,822 fail2ban.actions: WARNING [postfix] Ban 97.66.124.251
2014-10-23 13:17:42,694 fail2ban.actions: WARNING [postfix] Ban 124.200.250.27
2014-10-23 13:18:28,604 fail2ban.actions: WARNING [postfix] Ban 111.91.86.171
2014-10-23 13:18:35,479 fail2ban.actions: WARNING [postfix] Ban 123.18.208.252
2014-10-23 13:21:52,572 fail2ban.actions: WARNING [postfix] Ban 39.55.155.246
2014-10-23 13:21:59,394 fail2ban.actions: WARNING [postfix] Ban 122.167.201.219
2014-10-23 13:23:22,519 fail2ban.actions: WARNING [sasl] Ban 93.125.94.2
2014-10-23 13:23:34,367 fail2ban.actions: WARNING [postfix] Ban 221.158.66.84
2014-10-23 13:23:39,667 fail2ban.actions: WARNING [postfix] Ban 94.79.231.59
2014-10-23 13:25:58,138 fail2ban.actions: WARNING [postfix] Ban 5.160.183.163
2014-10-23 13:29:49,723 fail2ban.actions: WARNING [postfix] Ban 68.118.118.10
2014-10-23 13:30:06,548 fail2ban.actions: WARNING [postfix] Ban 50.250.213.34
2014-10-23 13:30:22,595 fail2ban.actions: WARNING [postfix] Ban 116.202.81.162
2014-10-23 13:31:57,825 fail2ban.actions: WARNING [postfix] Ban 39.32.186.142
2014-10-23 13:32:28,672 fail2ban.actions: WARNING [postfix] Ban 194.28.73.230
2014-10-23 13:32:39,027 fail2ban.actions: WARNING [postfix] Ban 113.173.24.237
2014-10-23 13:32:56,914 fail2ban.actions: WARNING [postfix] Ban 86.127.100.34
2014-10-23 13:36:51,449 fail2ban.actions: WARNING [postfix] Ban 121.167.24.204
2014-10-23 13:37:46,247 fail2ban.actions: WARNING [postfix] Ban 59.103.133.23
2014-10-23 13:39:40,248 fail2ban.actions: WARNING [postfix] Ban 1.53.13.143
2014-10-23 13:39:53,154 fail2ban.actions: WARNING [postfix] Ban 77.30.185.250
2014-10-23 13:41:21,550 fail2ban.actions: WARNING [postfix] Ban 14.141.111.226
2014-10-23 13:43:55,238 fail2ban.actions: WARNING [sasl] Ban 201.213.221.103
2014-10-23 13:45:26,703 fail2ban.actions: WARNING [postfix] Ban 124.200.250.26
2014-10-23 13:45:54,620 fail2ban.actions: WARNING [postfix] Ban 122.178.156.172
2014-10-23 13:45:57,720 fail2ban.actions: WARNING [postfix] Ban 176.121.227.102
2014-10-23 13:46:32,047 fail2ban.actions: WARNING [postfix] Ban 103.23.33.158
2014-10-23 13:47:55,975 fail2ban.actions: WARNING [postfix] Ban 122.169.58.113
2014-10-23 13:48:33,866 fail2ban.actions: WARNING [postfix] Ban 208.46.50.130
2014-10-23 13:49:49,784 fail2ban.actions: WARNING [postfix] Ban 167.135.119.251
2014-10-23 13:52:53,732 fail2ban.actions: WARNING [postfix] Ban 139.193.101.138
2014-10-23 13:53:33,484 fail2ban.actions: WARNING [postfix] Ban 43.252.101.98
2014-10-23 13:53:52,645 fail2ban.actions: WARNING [postfix] Ban 117.193.55.91
2014-10-23 13:53:59,459 fail2ban.actions: WARNING [postfix] Ban 121.101.186.118
2014-10-23 13:54:32,347 fail2ban.actions: WARNING [postfix] Ban 192.30.241.146
2014-10-23 13:54:35,170 fail2ban.actions: WARNING [postfix] Ban 209.181.18.217
2014-10-23 13:55:20,781 fail2ban.actions: WARNING [postfix] Ban 178.120.186.83
2014-10-23 13:57:58,082 fail2ban.actions: WARNING [sasl] Ban 87.197.159.118
2014-10-23 13:58:23,294 fail2ban.actions: WARNING [postfix] Ban 119.35.25.251
2014-10-23 14:00:33,406 fail2ban.actions: WARNING [postfix] Ban 94.97.129.113
2014-10-23 14:01:12,811 fail2ban.actions: WARNING [postfix] Ban 117.213.79.39
2014-10-23 14:04:49,980 fail2ban.actions: WARNING [postfix] Ban 115.112.33.53
2014-10-23 14:05:22,824 fail2ban.actions: WARNING [sasl] Ban 181.15.215.181
2014-10-23 14:05:49,183 fail2ban.actions: WARNING [postfix] Ban 121.130.137.95
2014-10-23 14:05:51,867 fail2ban.actions: WARNING [postfix] Ban 221.138.252.114
2014-10-23 14:06:29,756 fail2ban.actions: WARNING [postfix] Ban 198.0.71.201
2014-10-23 14:06:38,342 fail2ban.actions: WARNING [postfix] Ban 39.32.208.77
2014-10-23 14:08:17,665 fail2ban.actions: WARNING [sasl] Ban 70.196.64.104
2014-10-23 14:08:46,309 fail2ban.actions: WARNING [postfix] Ban 72.54.223.53
2014-10-23 14:09:26,133 fail2ban.actions: WARNING [postfix] Ban 151.64.98.8
2014-10-23 14:10:58,584 fail2ban.actions: WARNING [postfix] Ban 199.96.245.158
2014-10-23 14:13:49,421 fail2ban.actions: WARNING [postfix] Ban 91.241.224.135
2014-10-23 14:15:47,858 fail2ban.actions: WARNING [sasl] Ban 71.183.239.18
2014-10-23 14:16:33,898 fail2ban.actions: WARNING [postfix] Ban 74.202.252.56
2014-10-23 14:17:09,129 fail2ban.actions: WARNING [postfix] Ban 39.32.155.178
2014-10-23 14:18:08,113 fail2ban.actions: WARNING [postfix] Ban 12.25.8.201
2014-10-23 14:18:12,973 fail2ban.actions: WARNING [postfix] Ban 112.150.194.150
2014-10-23 14:18:54,821 fail2ban.actions: WARNING [postfix] Ban 64.16.141.26
2014-10-23 14:18:58,961 fail2ban.actions: WARNING [postfix] Ban 97.97.32.66
2014-10-23 14:19:42,557 fail2ban.actions: WARNING [postfix] Ban 115.241.116.191
2014-10-23 14:20:10,477 fail2ban.actions: WARNING [postfix] Ban 24.49.3.240
2014-10-23 14:21:46,013 fail2ban.actions: WARNING [sasl] Ban 98.101.135.206
2014-10-23 14:36:04,447 fail2ban.actions: WARNING [postfix] Ban 154.100.143.195
2014-10-23 14:37:43,726 fail2ban.actions: WARNING [sasl] Ban 76.187.73.212
2014-10-23 14:39:29,745 fail2ban.actions: WARNING [postfix] Ban 124.200.250.21
2014-10-23 15:42:01,739 fail2ban.actions: WARNING [sasl] Ban 111.248.45.220
2014-10-23 18:31:20,220 fail2ban.actions: WARNING [apache-wplogin] Ban 192.99.150.55
2014-10-23 19:39:30,989 fail2ban.actions: WARNING [apache-wplogin] Ban 104.151.230.82