As a follow on to my post about the slow cycle bot net it now looks like its slowing down (i.e. Fail2ban has blocked most of the compromised machines).
Scribblings from Steve
As a follow on to my post about the slow cycle bot net it now looks like its slowing down (i.e. Fail2ban has blocked most of the compromised machines).

Anyone who runs a server is used to it to being attacked by compromised machines which target their SSH services, their web services and their email services.
The attack on the email services takes two forms : either trying to relay email through the SMTP server or trying to break into the POP3 server using a list of known logons and a password list in a classic brute force attack. I use Fail2ban to control access to the SMTP and POP3/IMAP services and they’re pretty good at identifying rogues and firewalling them, but I still do manual checks from time to time.
The other day I noticed something … I was getting POP3/IMAP attempts at a very low rate, so slow in fact that Fail2ban didn’t notice them:
May 4 00:47:41 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 8 secs): user=<colin@a.domain.here>, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 4 21:49:14 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 5 08:38:48 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=<michael@a.domain.here>, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 5 14:00:00 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=<paul@a.domain.here>, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 5 23:39:19 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 6 03:27:11 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=<doug@a.domain.here>, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 6 13:11:27 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=<paul@a.domain.here>, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session= May 7 00:41:22 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session=<5Y+2iuNOpgBeiY4x> May 7 14:42:16 Debussy dovecot: imap-login: Disconnected (auth failed, 1 attempts in 7 secs): user=<doug@a.domain.here>, method=PLAIN, rip=94.137.142.49, lip=192.168.0.1, session=
But, I hear you say, why do I think there is a bot-net… it’s just one machine doing infrequent tests against the server…. and yes that’s what I though until I started grepping through the mail logs which produced this (the timestamps covered about 40 minutes). This output has not been sorted….
user=<richard@a.domain.here>, method=PLAIN, rip=60.170.102.230, user=<richard@a.domain.here>, method=PLAIN, rip=61.157.248.26, user=<richard>, method=PLAIN, rip=216.248.98.187, user=<postmaster@a.domain.here>, method=PLAIN, rip=218.77.80.51, user=<postmaster>, method=PLAIN, rip=117.245.10.224, user=<steve@a.domain.here>, method=PLAIN, rip=124.237.78.194, user=<steve>, method=PLAIN, rip=61.153.45.118, user=<drtone@a.domain.here>, method=PLAIN, rip=116.193.216.45, user=<drtone>, method=PLAIN, rip=61.190.99.62, user=<michael@a.domain.here>, method=PLAIN, rip=61.161.149.50, user=<michael>, method=PLAIN, rip=58.17.124.27, user=<paul@a.domain.here>, method=PLAIN, rip=58.17.221.4, user=<paul>, method=PLAIN, rip=221.176.112.45, user=<richard_s@a.domain.here>, method=PLAIN, rip=90.182.190.75, user=<richard_s>, method=PLAIN, rip=117.255.213.103, user=<richard@a.domain.here>, method=PLAIN, rip=125.74.189.200, user=<richard>, method=PLAIN, rip=223.244.233.13, user=<simon@a.domain.here>, method=PLAIN, rip=43.249.226.77, user=<simon>, method=PLAIN, rip=187.210.15.121, user=<colin@a.domain.here>, method=PLAIN, rip=218.106.153.152, user=<colin>, method=PLAIN, rip=193.150.73.22, user=<drtone@a.domain.here>, method=PLAIN, rip=193.164.95.16, user=<drtone>, method=PLAIN, rip=213.208.177.228, user=<doug@a.domain.here>, method=PLAIN, rip=218.22.96.76, user=<doug>, method=PLAIN, rip=221.212.18.14
So what we have here is multiple IP addresses all attacking my email server using addresses which are not being tried at random. So username@a.domain.here is always tried before username … even though the attempts come from different IP addresses. So something must be controlling these attempts
I put in a newfail2ban rule to trap dovecot Disconnect auth failed message like:
imap-login: Disconnected (auth failed, 1 attempts in 9 secs):
When I put this jail in the ban emails came flowing in… primarily from China, but some from OVH and some from GoDaddy.
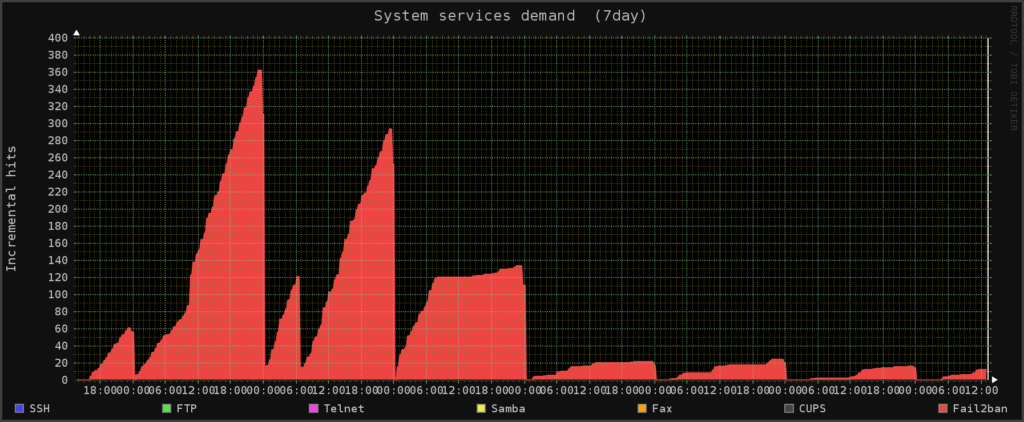
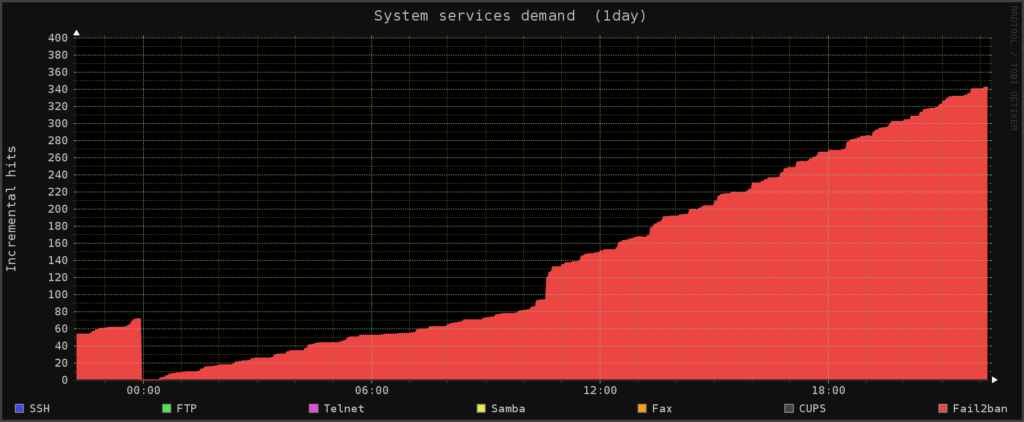
As at 19:30 on May 8th 653 IP addresses have been added to the firewall since I put the rule in just before Lunch on Sunday May 7th
Graph courtesy of Monitorix:
Its the list of usual suspects – China featuring high in the list of machines trying to break into servers (no surprises there) and OVH :
89.248.174.27
60.173.16.74
161.0.153.110
123.214.172.84
218.27.147.130
120.203.25.58
41.110.189.60
62.99.78.120
155.4.33.255
223.241.247.6
218.5.3.45
46.181.62.158
221.3.236.94
114.251.196.28
113.195.181.52
117.245.8.29
184.168.116.130
41.134.156.241
211.103.155.236
216.248.98.187
180.166.246.174
103.238.15.67
58.62.55.130
190.185.133.243
111.16.48.137
222.177.182.10
166.62.88.83
58.242.164.10
122.144.136.211
175.19.7.67
123.7.38.145
92.222.218.38
125.215.162.130
218.3.43.210
58.211.169.50
111.75.162.114
183.167.231.206
218.90.148.177
60.172.162.2
218.22.100.42
222.189.217.164
219.141.127.176
222.222.148.29
109.226.23.26
220.189.211.43
221.1.177.2
218.206.132.194
115.84.112.138
218.2.26.174
112.216.86.250
58.218.154.74
61.37.150.5
117.253.222.147
223.72.253.20
42.243.154.6
111.72.252.82
218.77.80.51
221.4.168.73
175.196.232.242
203.148.24.99
220.178.253.90
218.22.187.66
119.146.33.65
201.47.97.164
60.30.5.5
60.166.35.162
120.194.172.104
220.168.150.240
124.193.199.202
60.209.29.138
112.113.66.235
84.94.102.75
1.180.64.86
113.240.252.170
202.199.224.253
109.236.180.59
218.87.254.235
183.161.35.38
186.151.245.129
60.13.3.26
113.140.22.45
117.245.44.70
60.13.154.174
183.167.250.140
80.11.77.63
113.195.181.201
122.224.36.28
91.211.172.127
176.197.231.18
218.22.98.2
211.103.163.74
61.128.225.118
60.170.110.89
218.207.128.26
58.248.164.150
110.185.241.73
60.30.149.22
61.136.104.131
222.217.221.179
211.141.133.32
118.140.144.62
106.75.34.127
121.128.135.74
61.185.41.221
115.238.68.121
58.26.113.137
1.170.119.89
171.34.73.167
203.146.127.168
222.171.223.129
185.12.124.66
95.56.234.117
114.69.233.82
58.213.46.110
211.232.116.147
113.204.147.26
74.208.15.104
61.188.216.236
112.25.188.48
97.65.205.10
118.182.213.21
211.118.26.122
108.173.219.85
112.123.63.205
200.43.234.171
218.26.163.125
202.47.167.57
222.242.229.42
222.218.17.187
119.1.161.173
221.10.230.228
125.46.81.195
200.29.187.138
222.172.14.115
61.136.81.234
122.252.230.130
203.130.53.218
91.121.74.128
58.17.126.28
219.142.25.106
119.41.111.151
61.37.150.6
203.93.109.130
94.141.61.100
83.142.189.10
85.28.81.232
218.28.110.134
221.176.214.126
218.3.40.2
118.163.143.170
I tightened up the fail2ban rules after looking at my mail logs. The result is impressive but at the same time depressing … so many machines trying to break into my server. Several from GoDaddy…. I guess they’re starting to sit in the same place as OVH when it comes to hosting scum.