Anyone who runs a server is used to it to being attacked by compromised machines which target their SSH services, their web services and their email services.
The attack on the email services takes two forms : either trying to relay email through the SMTP server or trying to break into the POP3 server using a list of known logons and a password list in a classic brute force attack. I use Fail2ban to control access to the SMTP and POP3/IMAP services and they’re pretty good at identifying rogues and firewalling them, but I still do manual checks from time to time.
The other day I noticed something … I was getting POP3/IMAP attempts at a very low rate, so slow in fact that Fail2ban didn’t notice them:
May 4 00:47:41 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 8 secs): user=<colin@a.domain.here>, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=
May 4 21:49:14 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=, method=PLAIN, rip=94.137.142.49,
lip=192.168.0.1, session=
May 5 08:38:48 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=<michael@a.domain.here>, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=
May 5 14:00:00 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=<paul@a.domain.here>, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=
May 5 23:39:19 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=, method=PLAIN, rip=94.137.142.49,
lip=192.168.0.1, session=
May 6 03:27:11 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=<doug@a.domain.here>, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=
May 6 13:11:27 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=<paul@a.domain.here>, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=
May 7 00:41:22 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=<5Y+2iuNOpgBeiY4x>
May 7 14:42:16 Debussy dovecot: imap-login: Disconnected (auth failed,
1 attempts in 7 secs): user=<doug@a.domain.here>, method=PLAIN,
rip=94.137.142.49, lip=192.168.0.1, session=
But, I hear you say, why do I think there is a bot-net… it’s just one machine doing infrequent tests against the server…. and yes that’s what I though until I started grepping through the mail logs which produced this (the timestamps covered about 40 minutes). This output has not been sorted….
user=<richard@a.domain.here>, method=PLAIN, rip=60.170.102.230,
user=<richard@a.domain.here>, method=PLAIN, rip=61.157.248.26,
user=<richard>, method=PLAIN, rip=216.248.98.187,
user=<postmaster@a.domain.here>, method=PLAIN, rip=218.77.80.51,
user=<postmaster>, method=PLAIN, rip=117.245.10.224,
user=<steve@a.domain.here>, method=PLAIN, rip=124.237.78.194,
user=<steve>, method=PLAIN, rip=61.153.45.118,
user=<drtone@a.domain.here>, method=PLAIN, rip=116.193.216.45,
user=<drtone>, method=PLAIN, rip=61.190.99.62,
user=<michael@a.domain.here>, method=PLAIN, rip=61.161.149.50,
user=<michael>, method=PLAIN, rip=58.17.124.27,
user=<paul@a.domain.here>, method=PLAIN, rip=58.17.221.4,
user=<paul>, method=PLAIN, rip=221.176.112.45,
user=<richard_s@a.domain.here>, method=PLAIN, rip=90.182.190.75,
user=<richard_s>, method=PLAIN, rip=117.255.213.103,
user=<richard@a.domain.here>, method=PLAIN, rip=125.74.189.200,
user=<richard>, method=PLAIN, rip=223.244.233.13,
user=<simon@a.domain.here>, method=PLAIN, rip=43.249.226.77,
user=<simon>, method=PLAIN, rip=187.210.15.121,
user=<colin@a.domain.here>, method=PLAIN, rip=218.106.153.152,
user=<colin>, method=PLAIN, rip=193.150.73.22,
user=<drtone@a.domain.here>, method=PLAIN, rip=193.164.95.16,
user=<drtone>, method=PLAIN, rip=213.208.177.228,
user=<doug@a.domain.here>, method=PLAIN, rip=218.22.96.76,
user=<doug>, method=PLAIN, rip=221.212.18.14
So what we have here is multiple IP addresses all attacking my email server using addresses which are not being tried at random. So username@a.domain.here is always tried before username … even though the attempts come from different IP addresses. So something must be controlling these attempts
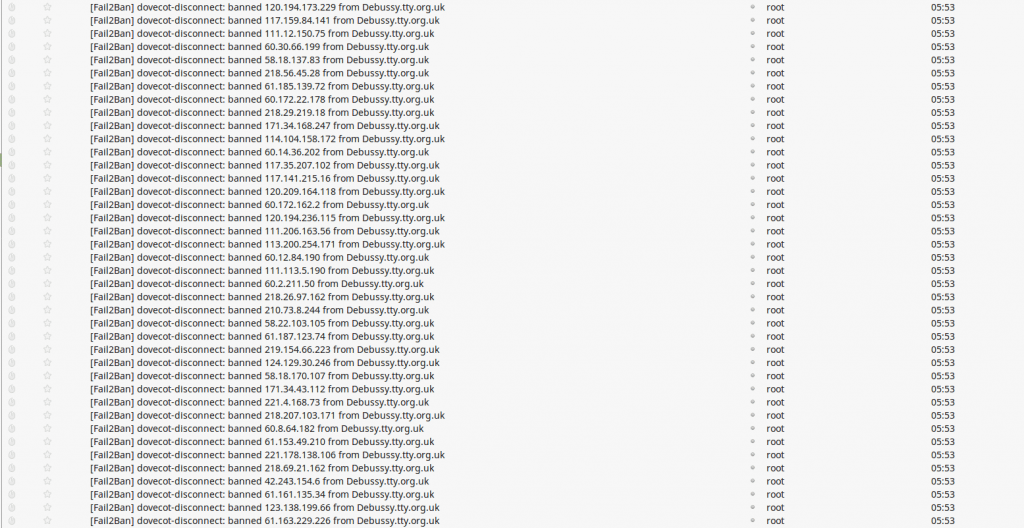
I put in a newfail2ban rule to trap dovecot Disconnect auth failed message like:
imap-login: Disconnected (auth failed, 1 attempts in 9 secs):
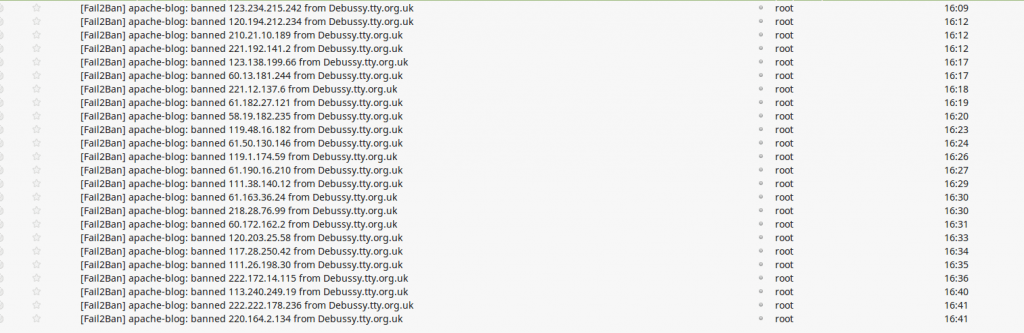
When I put this jail in the ban emails came flowing in… primarily from China, but some from OVH and some from GoDaddy.
As at 19:30 on May 8th 653 IP addresses have been added to the firewall since I put the rule in just before Lunch on Sunday May 7th