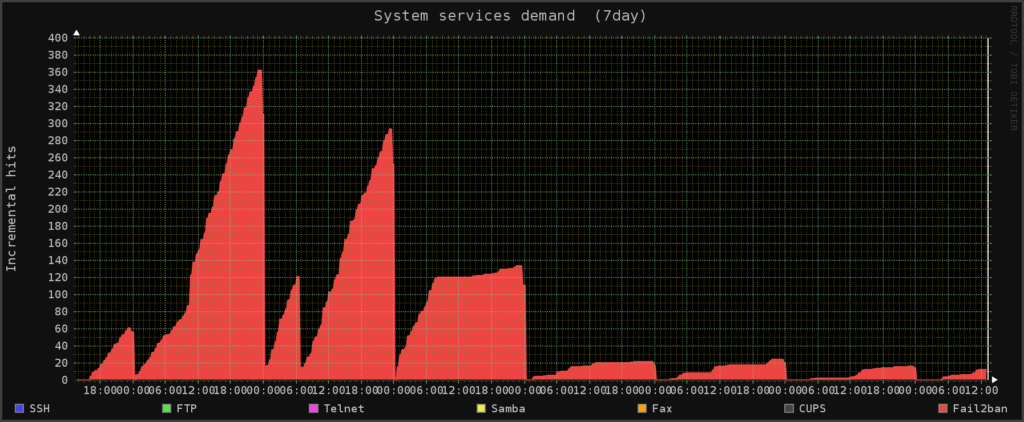
As a follow on to my post about the slow cycle bot net it now looks like its slowing down (i.e. Fail2ban has blocked most of the compromised machines).
Scribblings from Steve
As a follow on to my post about the slow cycle bot net it now looks like its slowing down (i.e. Fail2ban has blocked most of the compromised machines).

I have been seeing this as well lately. Although it probably has been going on for years. The probes are about 10 minutes apart, with the same pattern that you mention of trying first without the domain name and then with it. It rotates through several usernames, all but one non-existent on my system. The others are quite obscure – i.e. not guesses like ‘Fred’ or ‘John’, but combinations of names and numbers or just a fairly unusual name.
How did you set up fail2ban to block it?
I upped the monitor period and turned down the number of failed connections that can be made before Fail2ban firewalls them. I also put the userids in there too as most of them are not ones that exist and it was obvious they were only using a small number of names